Applies To: ThreatSync+ NDR, ThreatSync+ SaaS
ThreatSync+ policies continuously monitor your network for activity that violates the policies of your organization. Policies detect vulnerabilities and threats in your network and generate policy alerts if unauthorized activity is detected.
To minimize your response time and maximize your protection, it is important to configure and tune your policies to:
- Reflect the security policies of your organization.
- Apply policies only to parts of your network that your organizational policies govern.
- Reflect the appropriate severity for your organization.
To get started with ThreatSync+ policies, we recommend that you:
- Start with a small, manageable set of policies.
- Tune these policies so that you only receive alerts that are actionable — alerts that you can respond to and remediate so that the alert does not recur.
- Create additional policies that expand the protection of your network and tune them to prevent too many alerts.
For recommendations on how to tune your policies, go to Policy Tuning.
We recommend that you wait two to three days before you configure policies so ThreatSync+ can monitor and learn about your network.
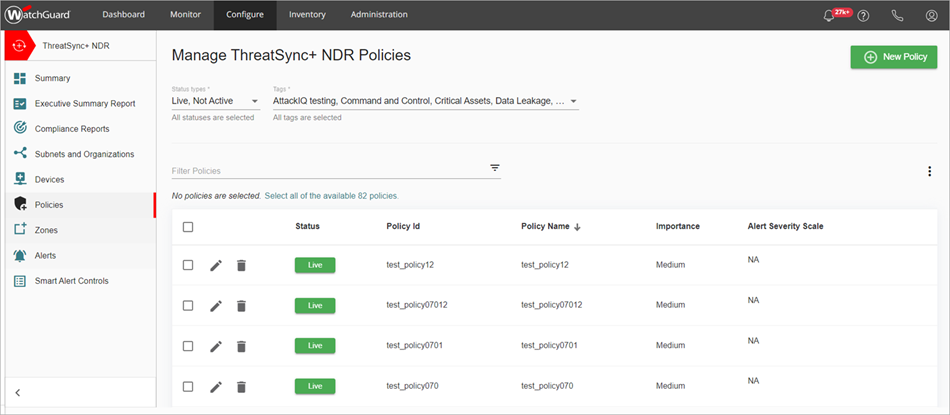
Enable Default ThreatSync+ Policies
ThreatSync+ NDR includes over 100 default policies that you can enable. . Because some default policies might not be appropriate for your network or your security policies, most default policies are disabled by default. Only a subset of Level 1 policies are enabled by default and automatically generate alerts. For a list of default policies, go to Default Policies and Zones.
Available default policies depend on your license. For information about ThreatSync+ SaaS policies, go to Level 1 Policies for ThreatSync+ SaaS — Microsoft 365.
If you enable a large number of default policies, you might receive more alerts than you can respond to. If you enable too few policies, you might miss important alerts about possible threats in your network.
To enable a default ThreatSync+ policy:
- Log in to your WatchGuard Cloud account.
- Select Configure > ThreatSync+ > Policies.
- Next to the default policy you want to enable, click Not Active.
The policy status changes to Live.
Add Custom ThreatSync+ Policies
You can create a new ThreatSync+ policy and customize policy definitions for your network. Each policy evaluates all traffic or event logs between a source zone and a destination zone and triggers an alert when specific conditions are met. These conditions are activity triggers.
For more information, go to Policy Evaluation.
To add a custom ThreatSync+ policy:
- Log in to your WatchGuard Cloud account.
- Select Configure > ThreatSync+ > Policies.
- On the Manage ThreatSync+ Policies page, click New Policy.
The Create a New Policy page opens.
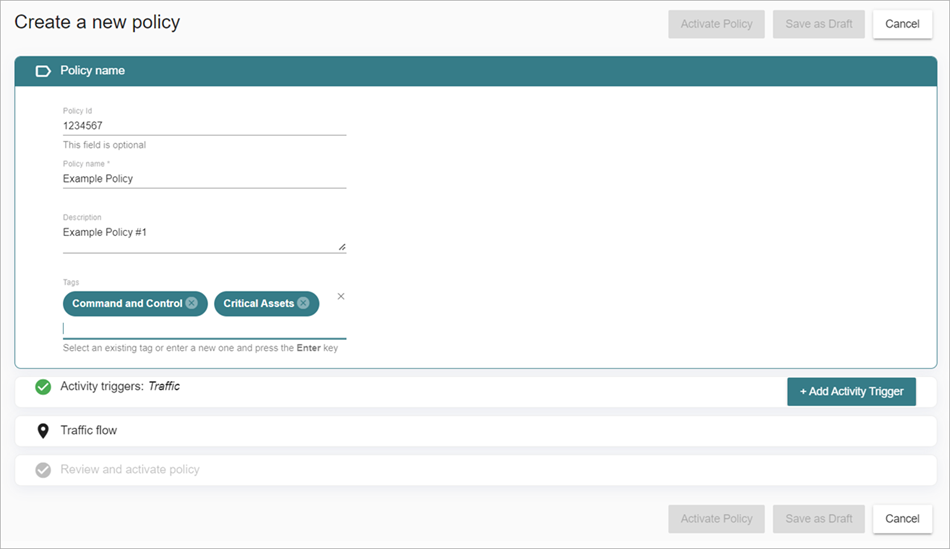
- (Optional) In the Policy ID text box, enter a policy ID.
The policy ID uniquely identifies the policy. If you create a custom defense goal report with the Compliance Reporting license, you might want to reference a custom policy in one of the controls defined in the defense goal. Use this policy ID to uniquely identify the policy. If you do not enter a policy ID, ThreatSync+ assigns it for you. For more information about compliance reporting, go to About WatchGuard Compliance Reporting.
- In the Policy Name text box, enter a name for your new policy.
- Enter a description.
- In the Tags text box, select or create tags to apply to your policy.
- Click Activity Triggers.
The Activity Triggers section expands. - In the Activity Triggers section, select what type of activity you want to set the alert for: Traffic, Anomalies, or Service Events.
- From the Importance drop-down list, select the importance to assign to your activity: Very Low, Low, Medium, High, or Very High.
- If you only want to receive alerts for specific traffic, select Alert on Specific Traffic and specify the alert conditions.
- If you only want to receive alerts for specific anomalies, select Alert on Specific Anomalies and specify the alert conditions.
- If you only want to receive alerts for specific service events, select Alert on Specific Service Events and specify the alert conditions.
- Click Traffic Flow.
The Traffic Flow section expands. - Configure the source and destination traffic flow settings. If you want to create a new zone, click Create a Zone to go to the Zones page. For more information, go to Manage ThreatSync+ Zones.
- Review your policy details.
- Activate your policy or save it as a draft to review later.
Activate or Deactivate ThreatSync+ Policies
On the Manage Policies page, you can activate or deactivate one or more policies. When you activate a policy, ThreatSync+ detects violations of the access policies of your organization and generates policy alerts to notify you about policy violations.
Default policies are similar to templates. When you activate or edit a default policy, ThreatSync+ saves a copy of the policy for you. If you delete your copy, any changes you made to the policy definition are discarded and the policy reverts back to the default policy definition. For more information, go to About ThreatSync+ Policies and Zones.
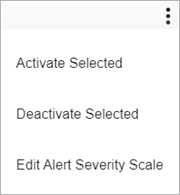
To activate or deactivate a ThreatSync+ policy, from the Manage Polices page:
- Select one or more policies you want to edit.
- Click
 .
. - Select Activate Selected or Deactivate Selected.
- You can also click Live in the Status column to deactivate the policy and change the status to Not Active, or click Not Active to activate the policy and change the status to Live.
Edit the Policy Alert Severity Scale
For policy alerts that are based on machine learning, ThreatSync+ builds a baseline of activity and generate alerts only when traffic varies from this baseline. For example, an unexpected large volume of data sent to the Internet generates an alert because it varies substantially from the baseline activity.
If you want to generate fewer alerts, you can adjust the alert sensitivity to make the detection less sensitive.

To edit the Alert Severity Scale for a specific ThreatSync+ policy:
- On the Manage ThreatSync+ Policies page, click
 next to the policy you want to edit.
next to the policy you want to edit.
The Policy Details page opens. - In the Activity Triggers section, next to Alert Severity Scale, click
 .
.
The Edit Alert Severity Scale dialog box opens.
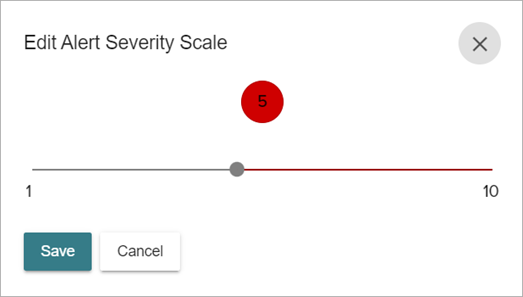
- To change the Alert Severity Scale, drag the slider to a new value. To generate fewer alerts, select a higher value. To generate more alerts, select a lower value.
- Click Save.
You can also edit the Alert Severity Scale on the Traffic page when specific anomaly types are selected with the Events Data Source. For more information, go to Investigate ThreatSync+ Traffic.